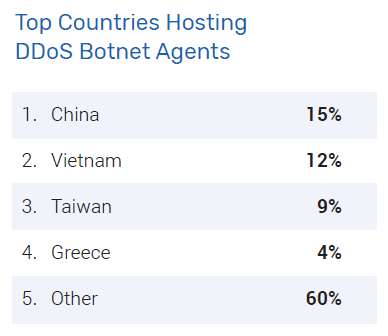
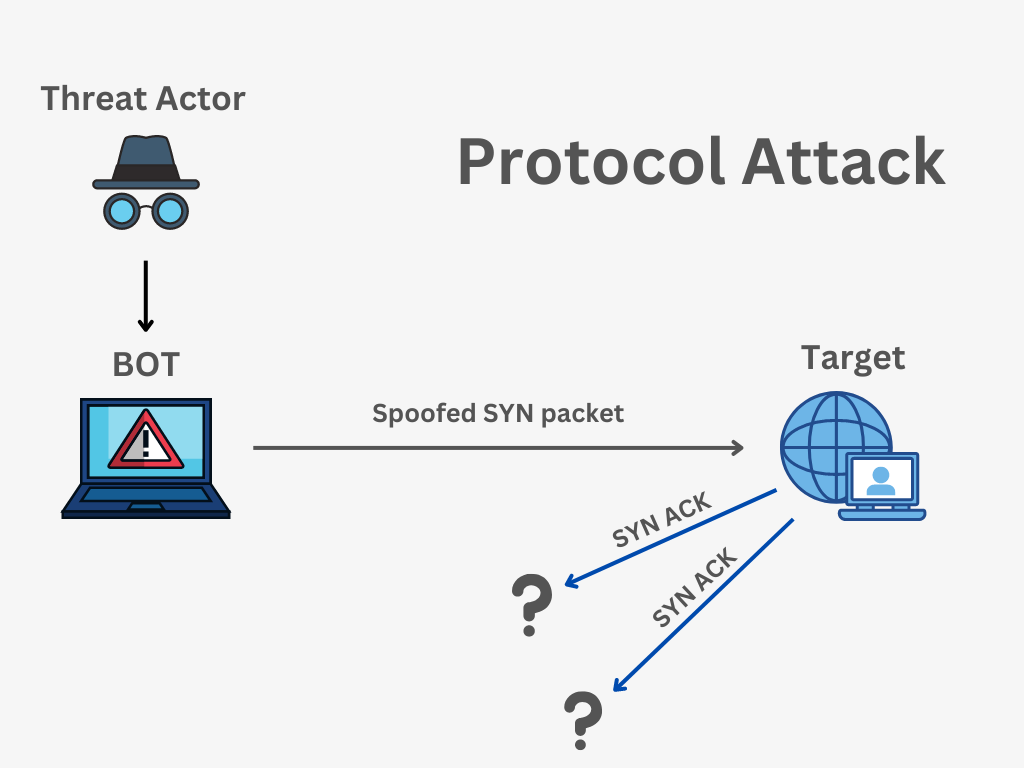
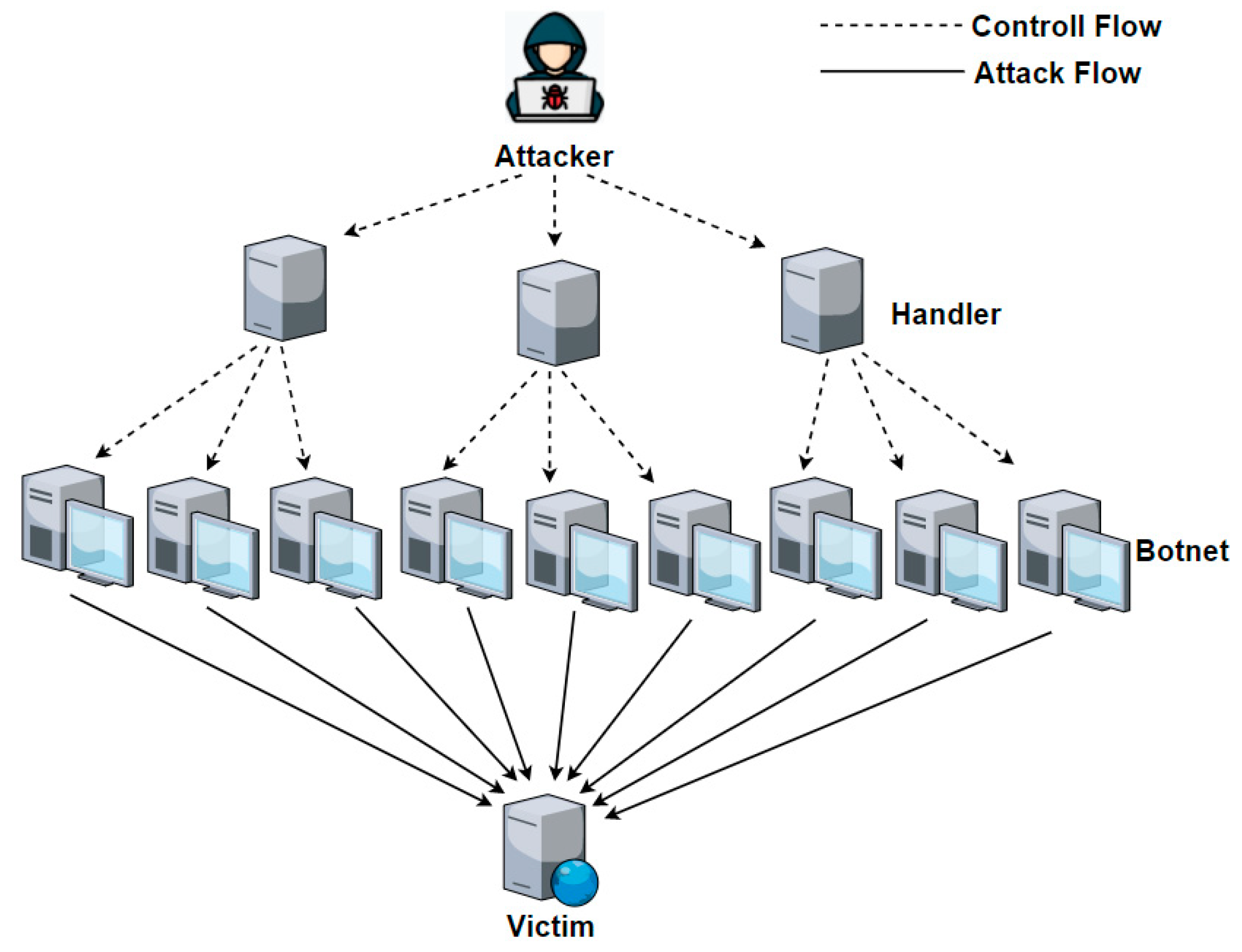
Shadowserver on X: "Two new daily honeypot drone based DDoS reports have been enabled! Honeypot DDoS Events Report contains info on C2s issuing attack commands to Mirai-like infected IoT devices: https://t.co/iauDYJXrLM Honeypot
Securing Against DoS/DDoS Attacks in Internet of Flying Things using Experience-based Deep Learning Algorithm

Bob and Chip crack DDoS cases over a cuppa in Chapter 2. | Kunal Makwana posted on the topic | LinkedIn

Plane-tracking site Flight Radar 24 DDoSed... just as drones spotted buzzing over Azerbaijan and Armenia • The Register
Applied Sciences | Free Full-Text | Detection of Unknown DDoS Attacks with Deep Learning and Gaussian Mixture Model

Run time variation with increasing number of UAVs for DDoS attack (same... | Download Scientific Diagram

Today's D Brief: Small gains by Ukraine, Russia; Hamas incursions slow; Army's anti-drone gear; Biggest DDoS attack ever?; And a bit more. - Defense One
Securing Against DoS/DDoS Attacks in Internet of Flying Things using Experience-based Deep Learning Algorithm
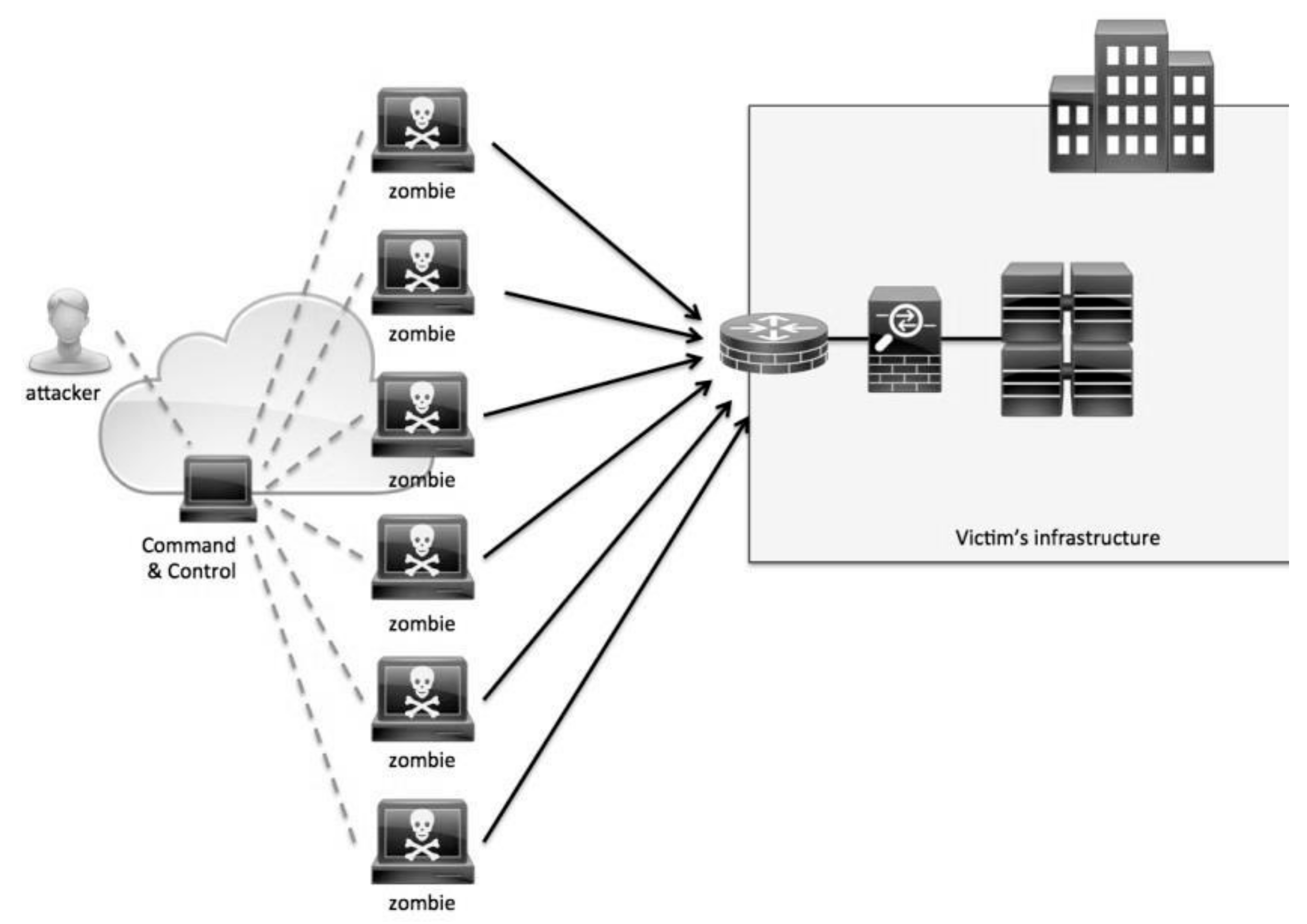
Symmetry | Free Full-Text | Distributed Denial of Service (DDoS) Mitigation Using Blockchain—A Comprehensive Insight




![PDF] The Impact of DoS Attacks on the AR.Drone 2.0 | Semantic Scholar PDF] The Impact of DoS Attacks on the AR.Drone 2.0 | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/3eaba6abfaf1bb8c712b7a2bd8baaad5d8dec2ef/3-Figure1-1.png)